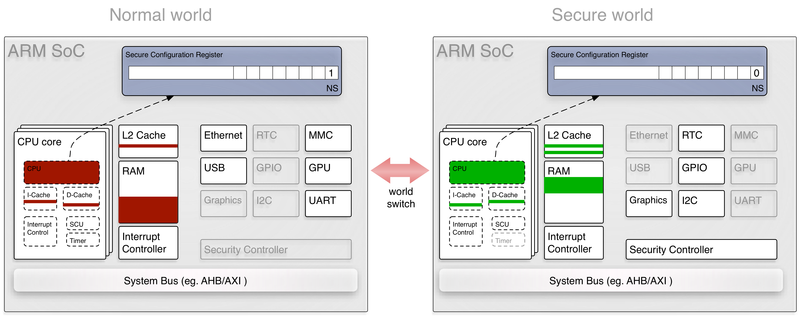
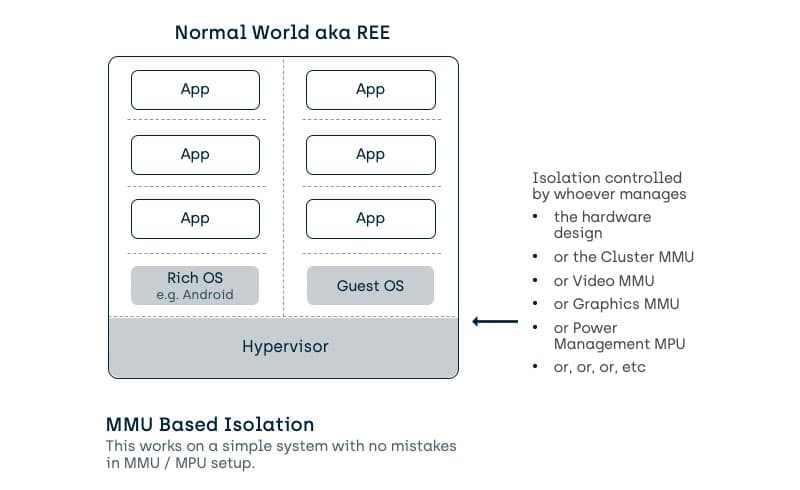
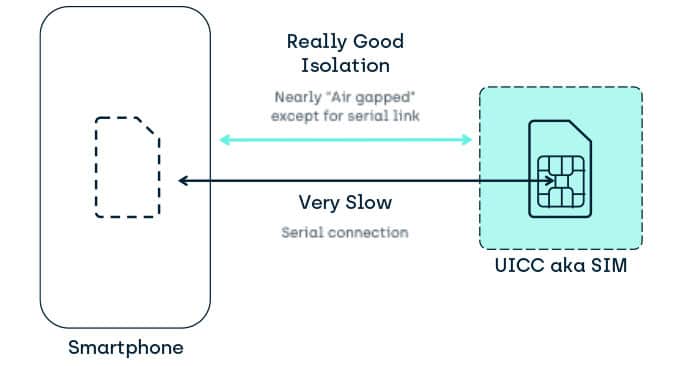
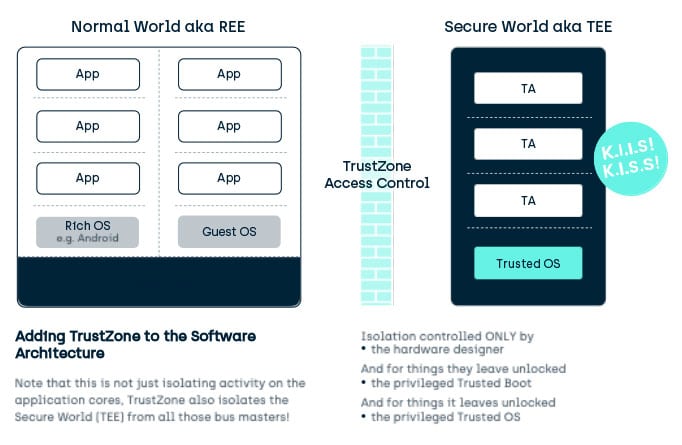
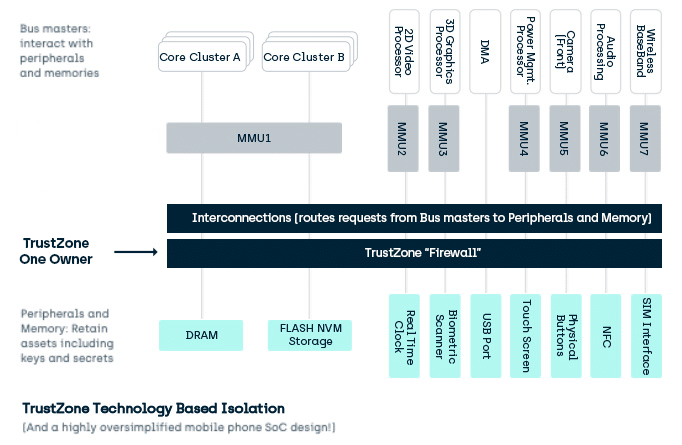
Investigating ARM Cortex® M33 core with TrustZone® – transition from non-secure to secure world | MCU on Eclipse

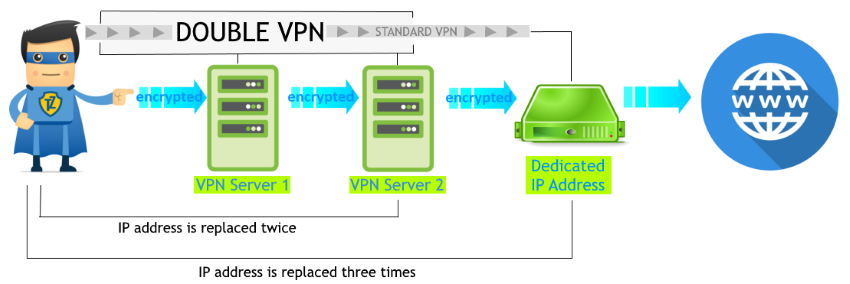
Trust.Zone VPN Review 2021: fast, secure & convenient » VPNTester.net - the real VPN comparison site
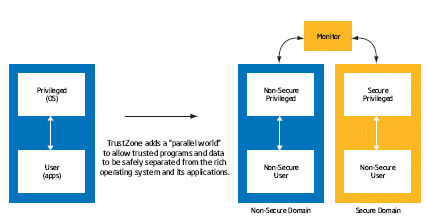
ARM Security Solutions and Intel Authenticated Flash -- How to integrate Intel Authenticated Flash with ARM TrustZone for maximum system protection
![System example partitioning secure and non-secure area with TrustZone [2]. | Download Scientific Diagram System example partitioning secure and non-secure area with TrustZone [2]. | Download Scientific Diagram](https://www.researchgate.net/profile/Mariagiovanna-Sami/publication/4278172/figure/fig1/AS:669986985091101@1536748753954/System-example-partitioning-secure-and-non-secure-area-with-TrustZone-2.png)
System example partitioning secure and non-secure area with TrustZone [2]. | Download Scientific Diagram