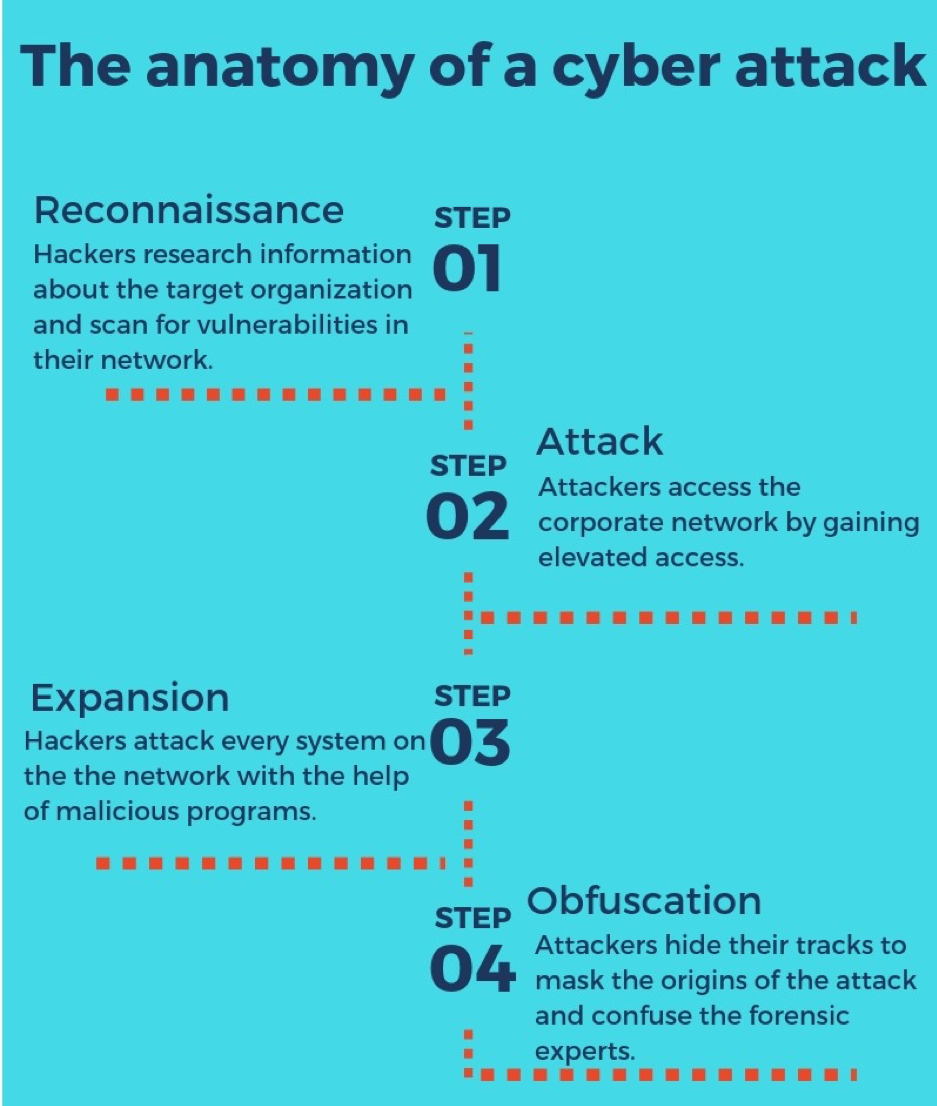
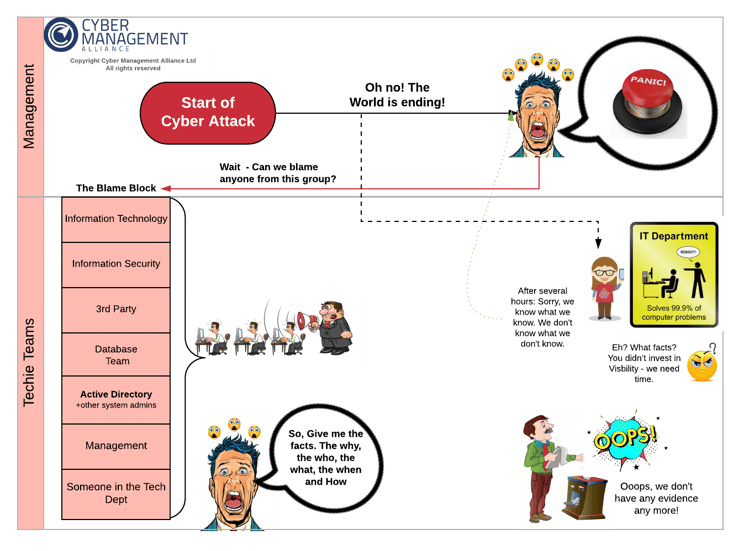
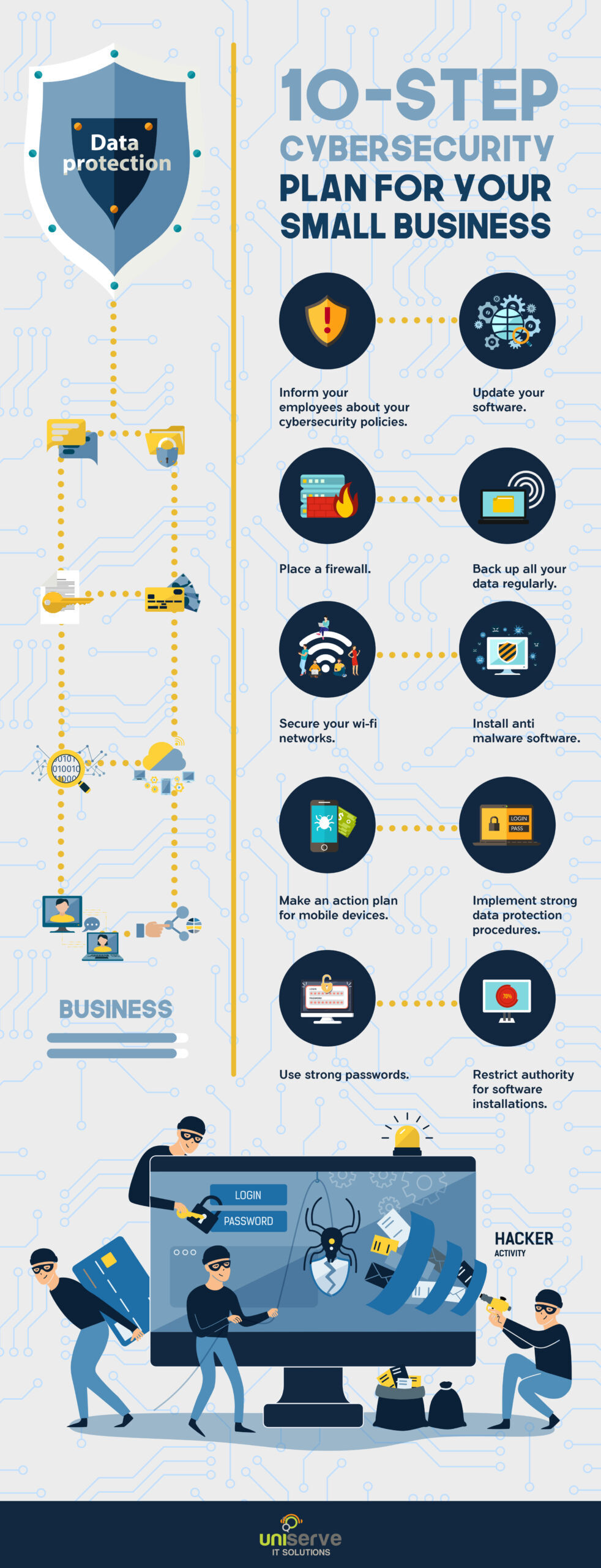
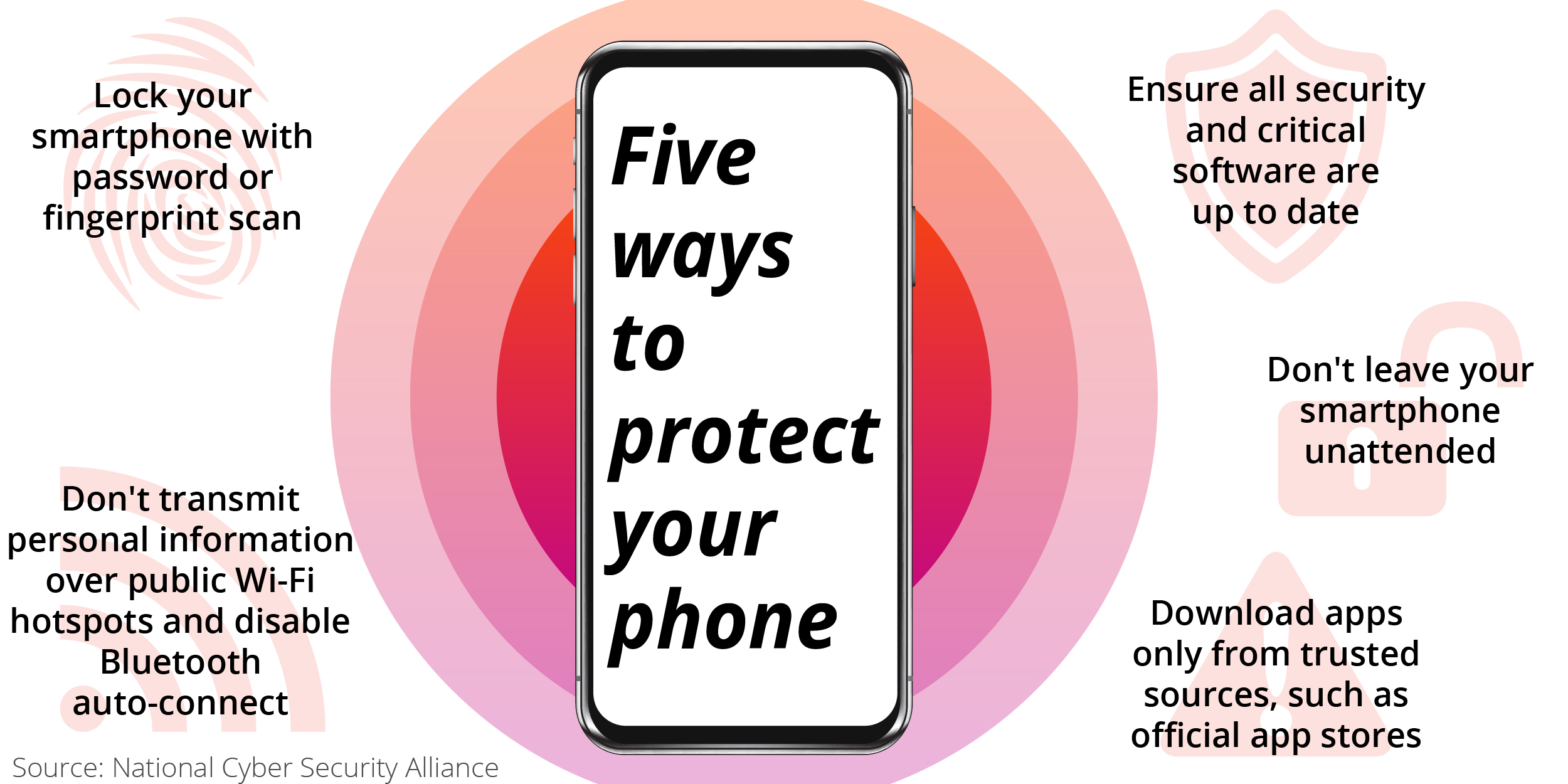
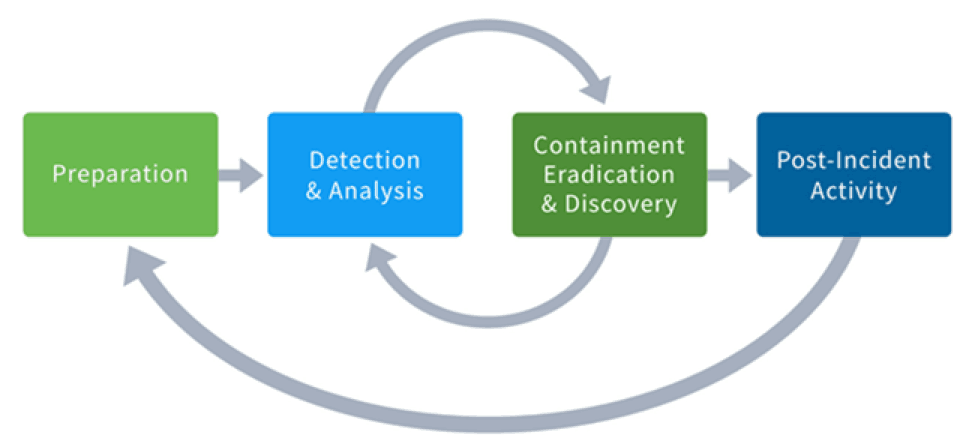
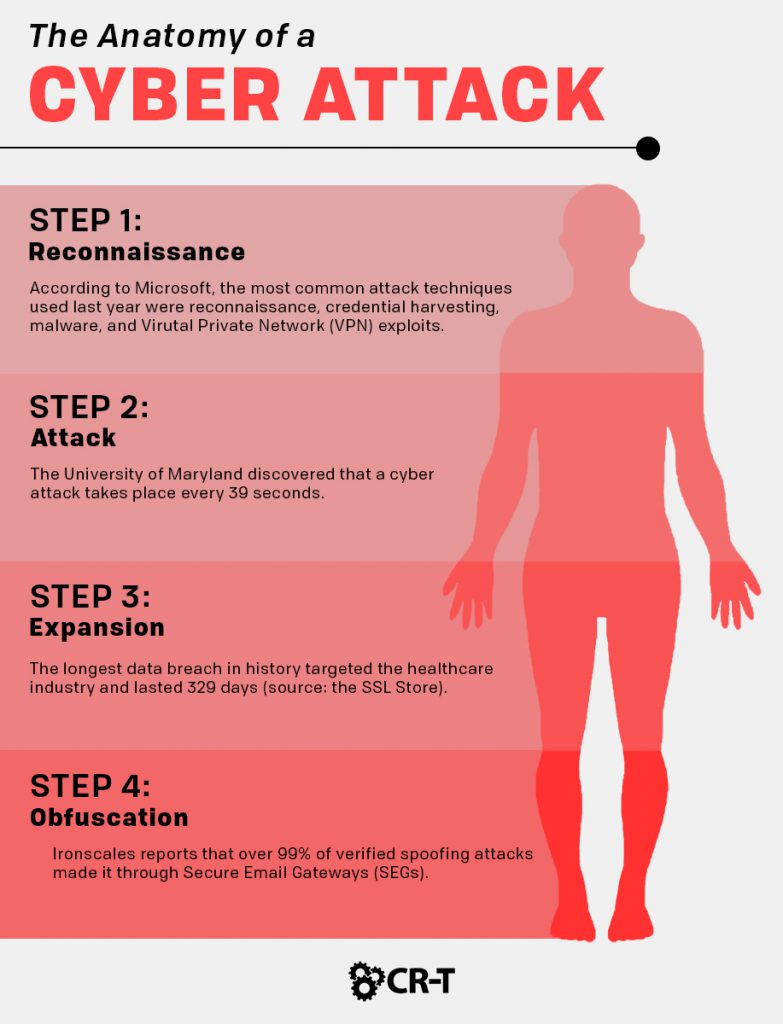
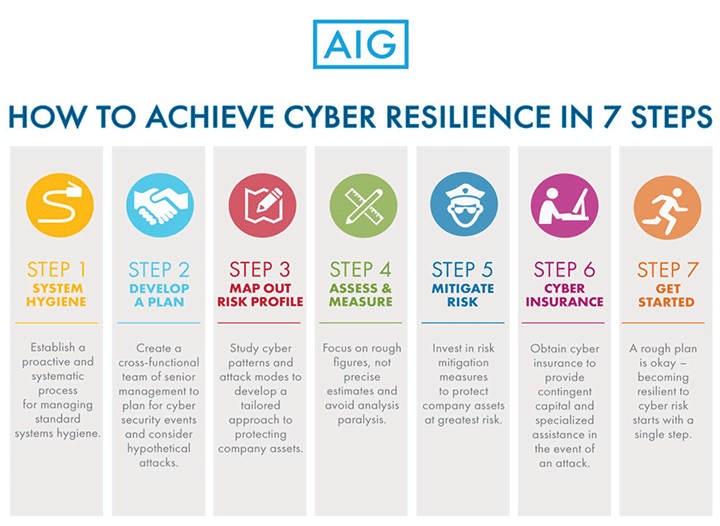
FIT Cybersecurity - Containment, eradication, and recovery are the three essential steps that every business should take after a cyberattack incident. Through these steps, we can isolate the attack and learn from
![NIL - ⚠️ [𝗨𝗡𝗗𝗘𝗥𝗦𝗧𝗔𝗡𝗗𝗜𝗡𝗚 𝗧𝗛𝗘 𝗜𝗠𝗣𝗢𝗥𝗧𝗔𝗡𝗖𝗘 𝗢𝗙 𝗙𝗜𝗥𝗦𝗧 𝗦𝗧𝗘𝗣𝗦 𝗔𝗙𝗧𝗘𝗥 𝗔 𝗥𝗔𝗡𝗦𝗢𝗠𝗪𝗔𝗥𝗘 𝗔𝗧𝗧𝗔𝗖𝗞] 📈 Check out the 𝘀𝘁𝗲𝗽𝘀 𝘆𝗼𝘂 𝘀𝗵𝗼𝘂𝗹𝗱 𝘁𝗮𝗸𝗲 when you discover a cyber incident and tips on ... NIL - ⚠️ [𝗨𝗡𝗗𝗘𝗥𝗦𝗧𝗔𝗡𝗗𝗜𝗡𝗚 𝗧𝗛𝗘 𝗜𝗠𝗣𝗢𝗥𝗧𝗔𝗡𝗖𝗘 𝗢𝗙 𝗙𝗜𝗥𝗦𝗧 𝗦𝗧𝗘𝗣𝗦 𝗔𝗙𝗧𝗘𝗥 𝗔 𝗥𝗔𝗡𝗦𝗢𝗠𝗪𝗔𝗥𝗘 𝗔𝗧𝗧𝗔𝗖𝗞] 📈 Check out the 𝘀𝘁𝗲𝗽𝘀 𝘆𝗼𝘂 𝘀𝗵𝗼𝘂𝗹𝗱 𝘁𝗮𝗸𝗲 when you discover a cyber incident and tips on ...](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=10165606280495162)
NIL - ⚠️ [𝗨𝗡𝗗𝗘𝗥𝗦𝗧𝗔𝗡𝗗𝗜𝗡𝗚 𝗧𝗛𝗘 𝗜𝗠𝗣𝗢𝗥𝗧𝗔𝗡𝗖𝗘 𝗢𝗙 𝗙𝗜𝗥𝗦𝗧 𝗦𝗧𝗘𝗣𝗦 𝗔𝗙𝗧𝗘𝗥 𝗔 𝗥𝗔𝗡𝗦𝗢𝗠𝗪𝗔𝗥𝗘 𝗔𝗧𝗧𝗔𝗖𝗞] 📈 Check out the 𝘀𝘁𝗲𝗽𝘀 𝘆𝗼𝘂 𝘀𝗵𝗼𝘂𝗹𝗱 𝘁𝗮𝗸𝗲 when you discover a cyber incident and tips on ...

5 Actionable Steps To Secure Your Business From Cyber Attacks - Digital Brand Protection – FraudWatch

10 Steps to Cybersecurity During a Pandemic - The Fulcrum Group 10 Steps to Cybersecurity During a Pandemic