GitHub - chriswayg/tor-server: An efficient and secure Tor relay server Docker image based on Debian

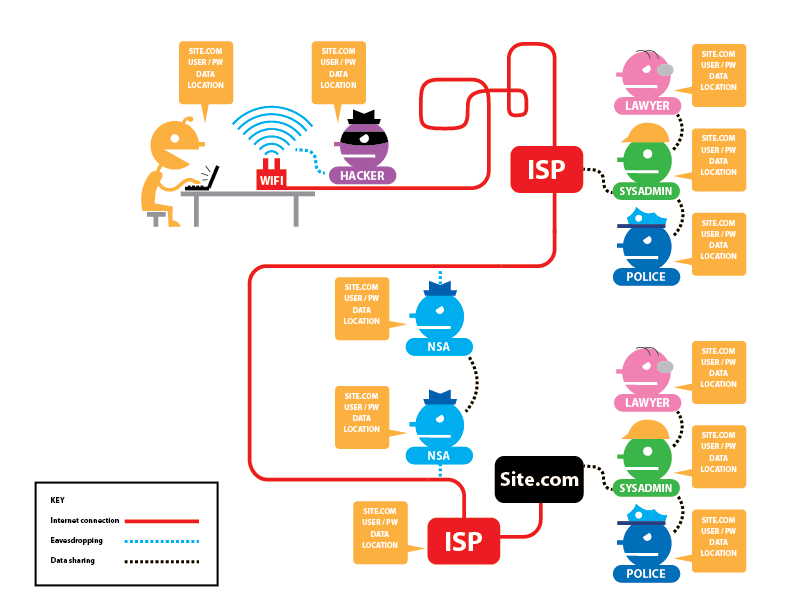
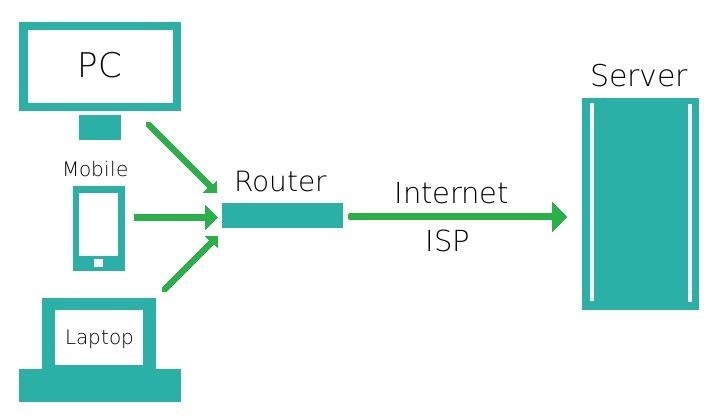
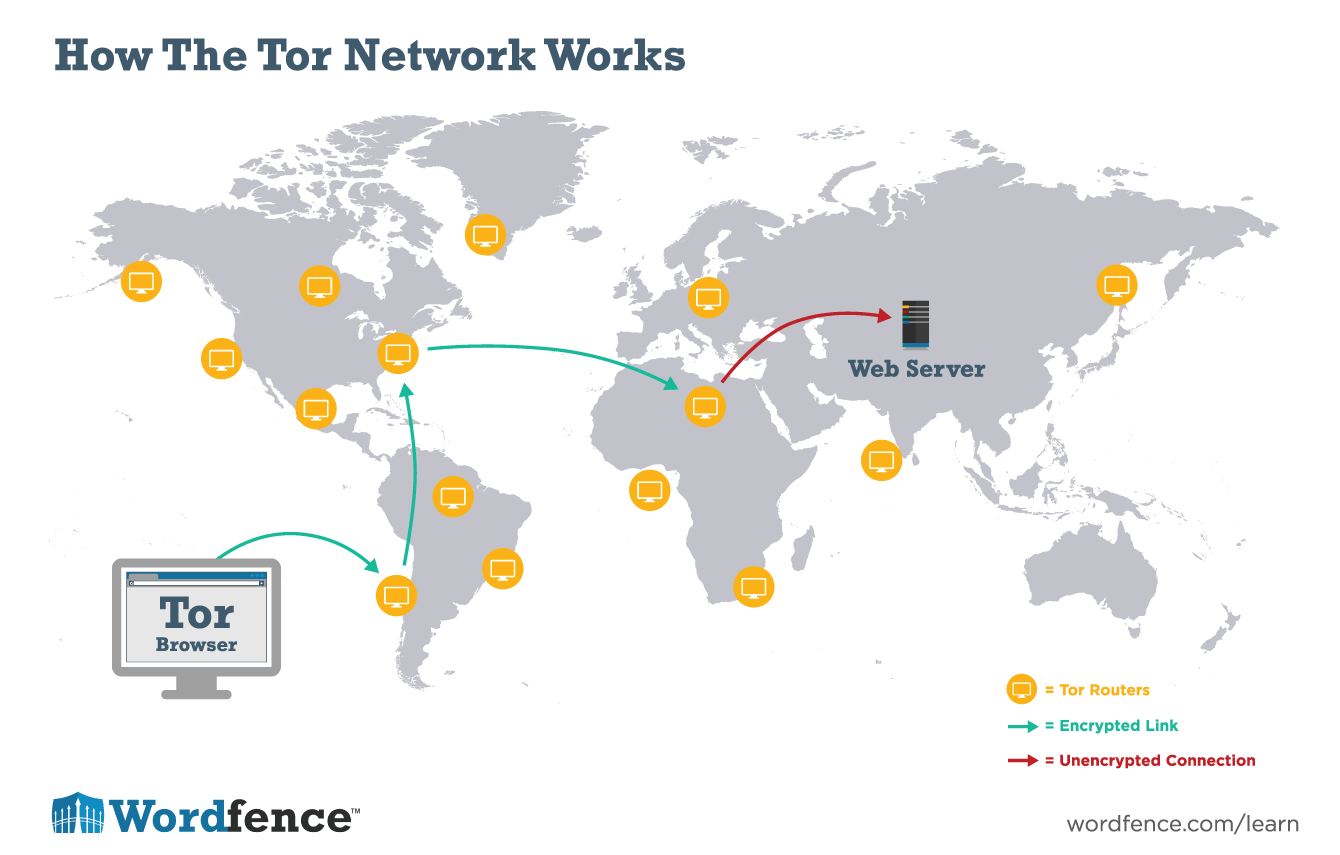
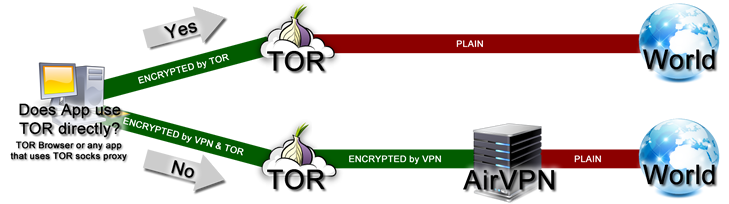
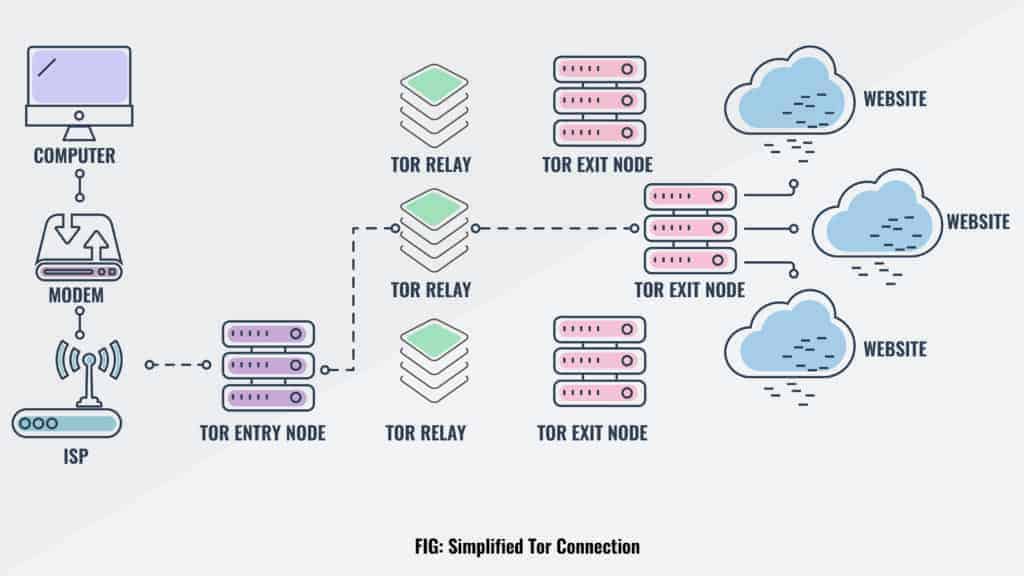
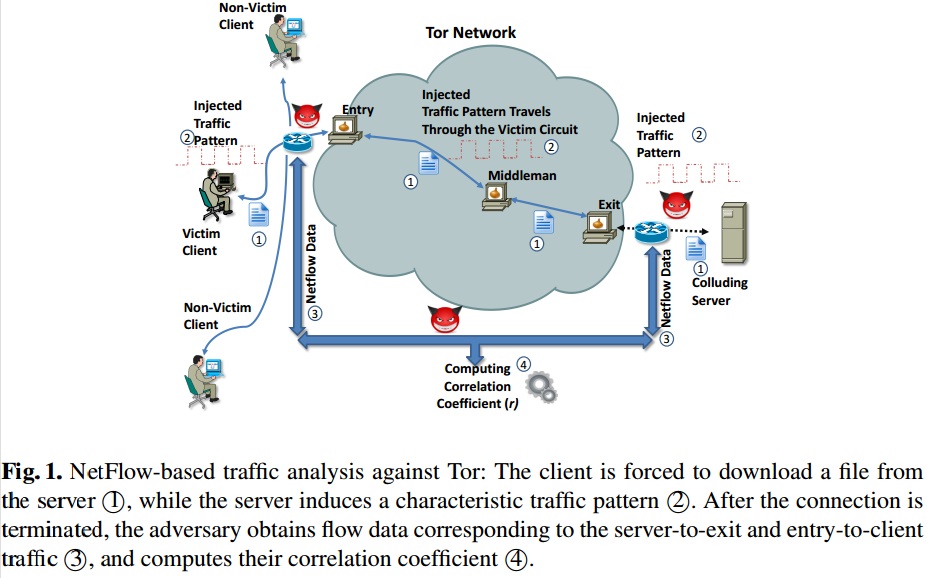
Europol - Tor (The Onion Router) is a free network designed to anonymise real Internet Protocol (IP) addresses by routing traffic through many servers of the Tor network. Tor is used by