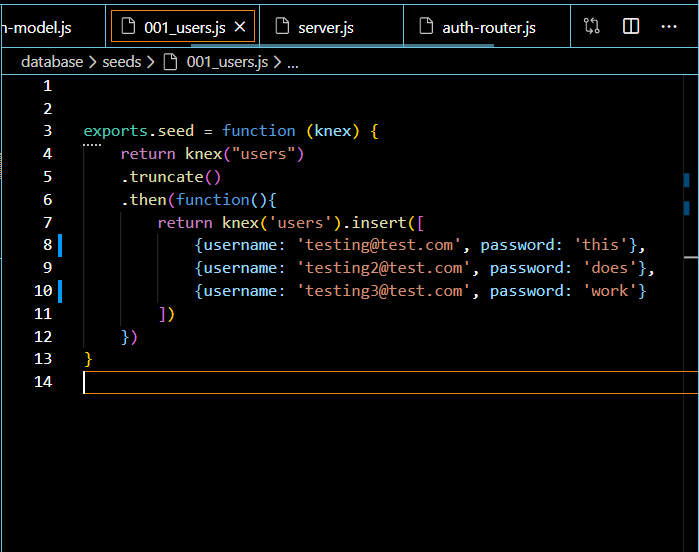
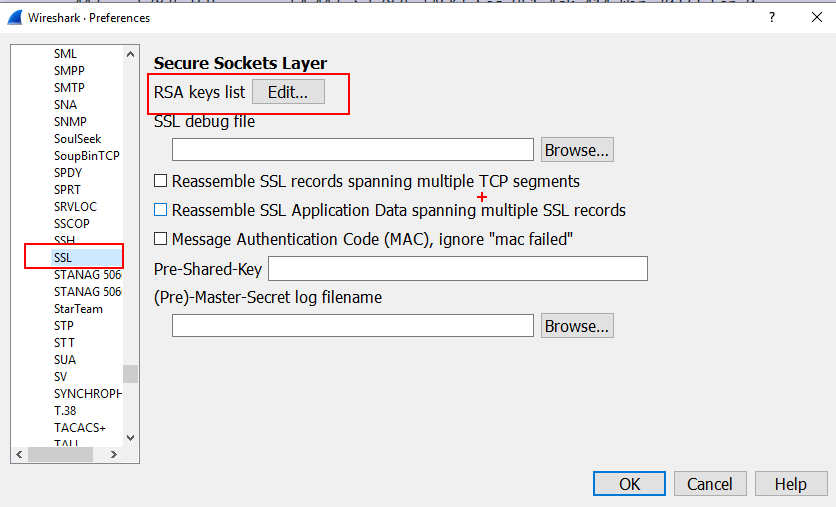
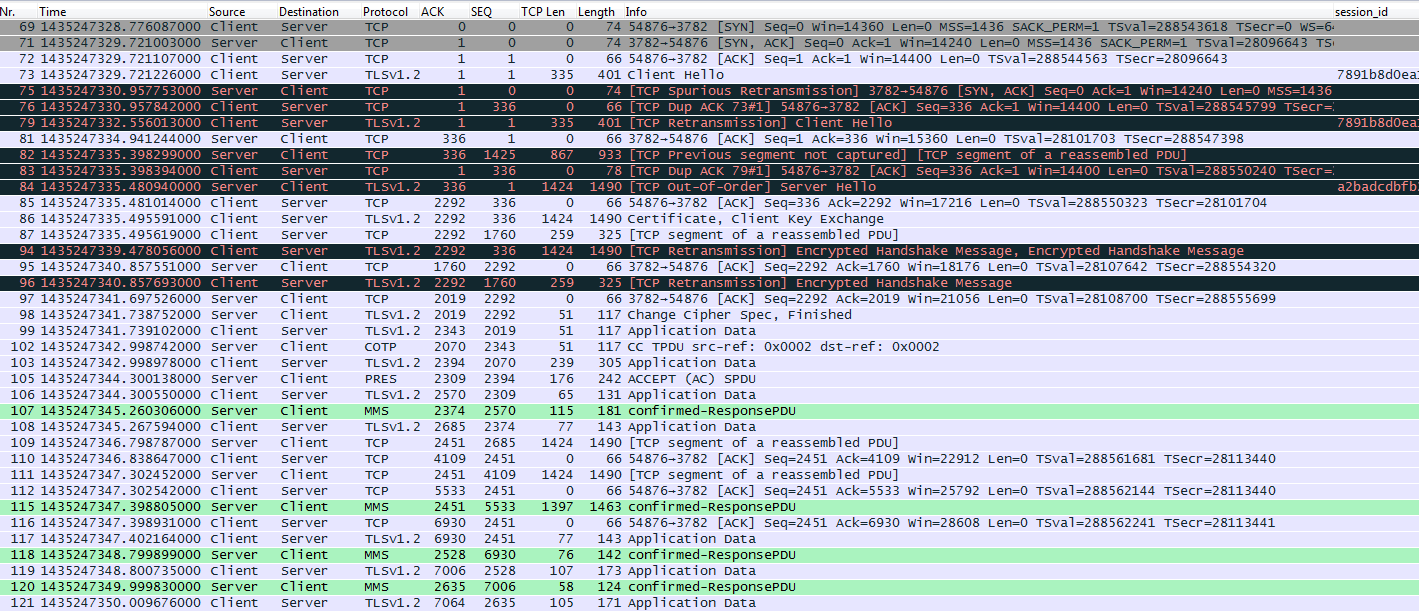
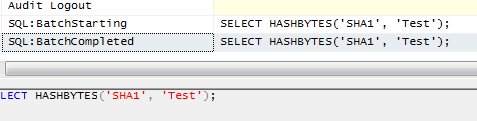
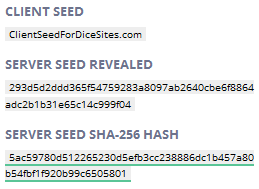
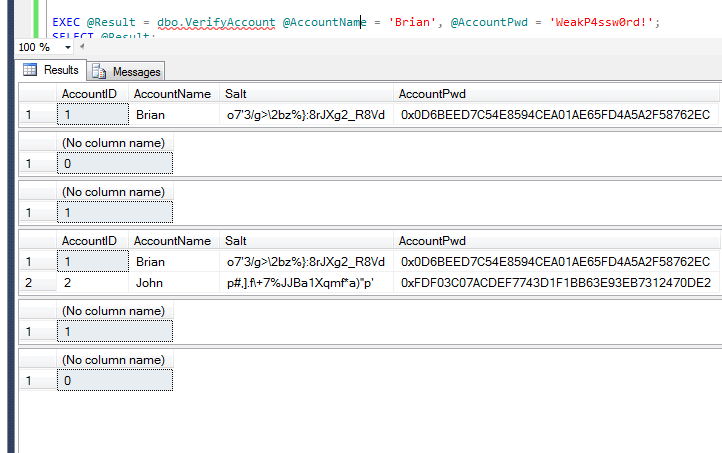
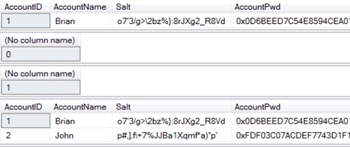
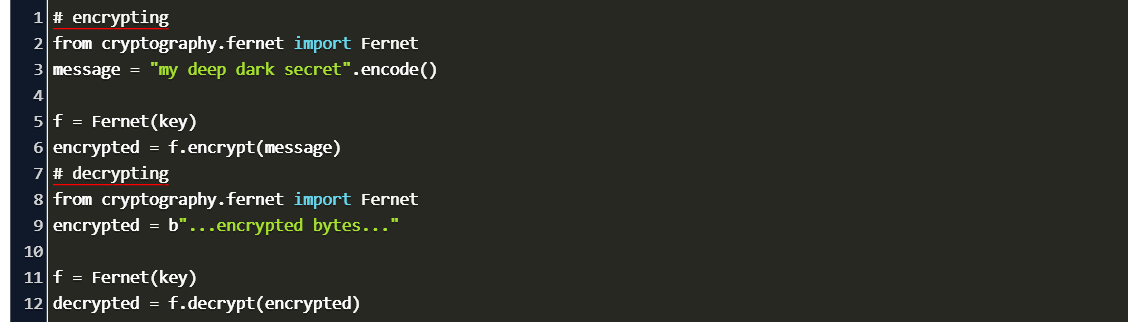
SQL Server - Encrypting Passwords with Symmetric Encryption Functions ENCRYPTBYPASSPHRASE and DECRYPTBYPASSPHRASE - Dirceu Resende

Cisco Talos Intelligence Group - Comprehensive Threat Intelligence: Research Spotlight: The Resurgence of Qbot
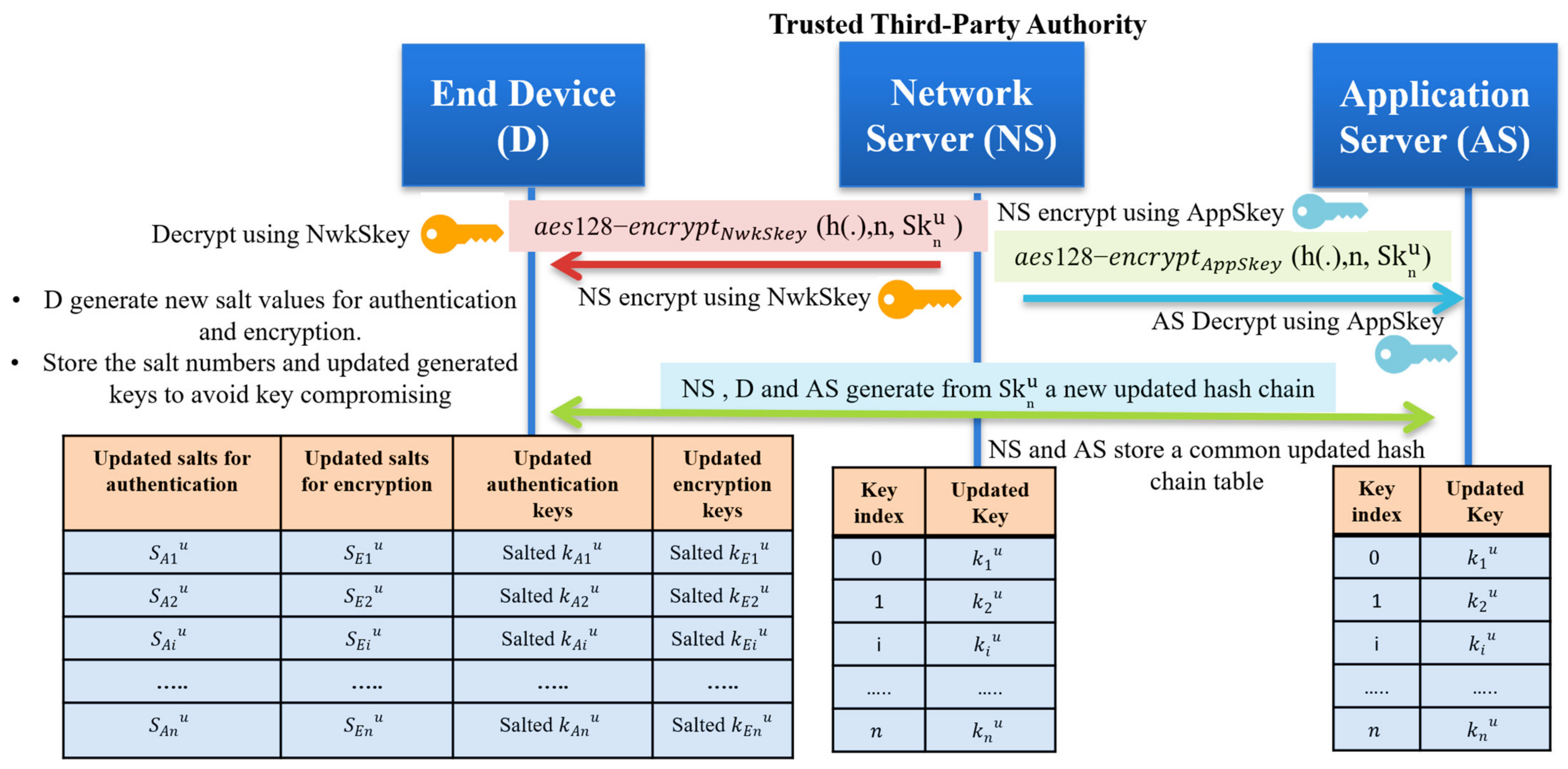
Sensors | Free Full-Text | A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks | HTML

SQL Server - Encrypting Passwords with Symmetric Encryption Functions ENCRYPTBYPASSPHRASE and DECRYPTBYPASSPHRASE - Dirceu Resende

Cisco Talos Intelligence Group - Comprehensive Threat Intelligence: Research Spotlight: The Resurgence of Qbot