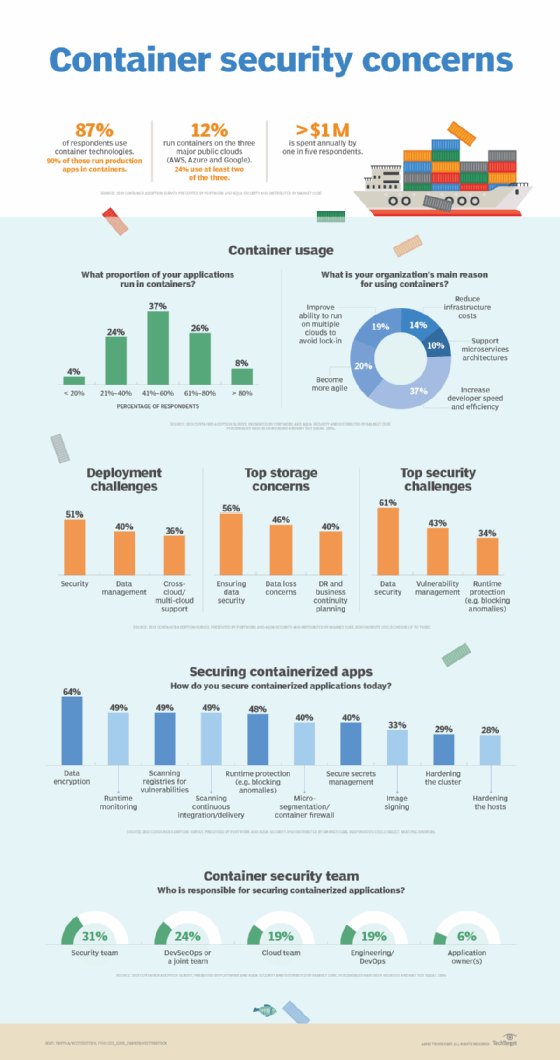
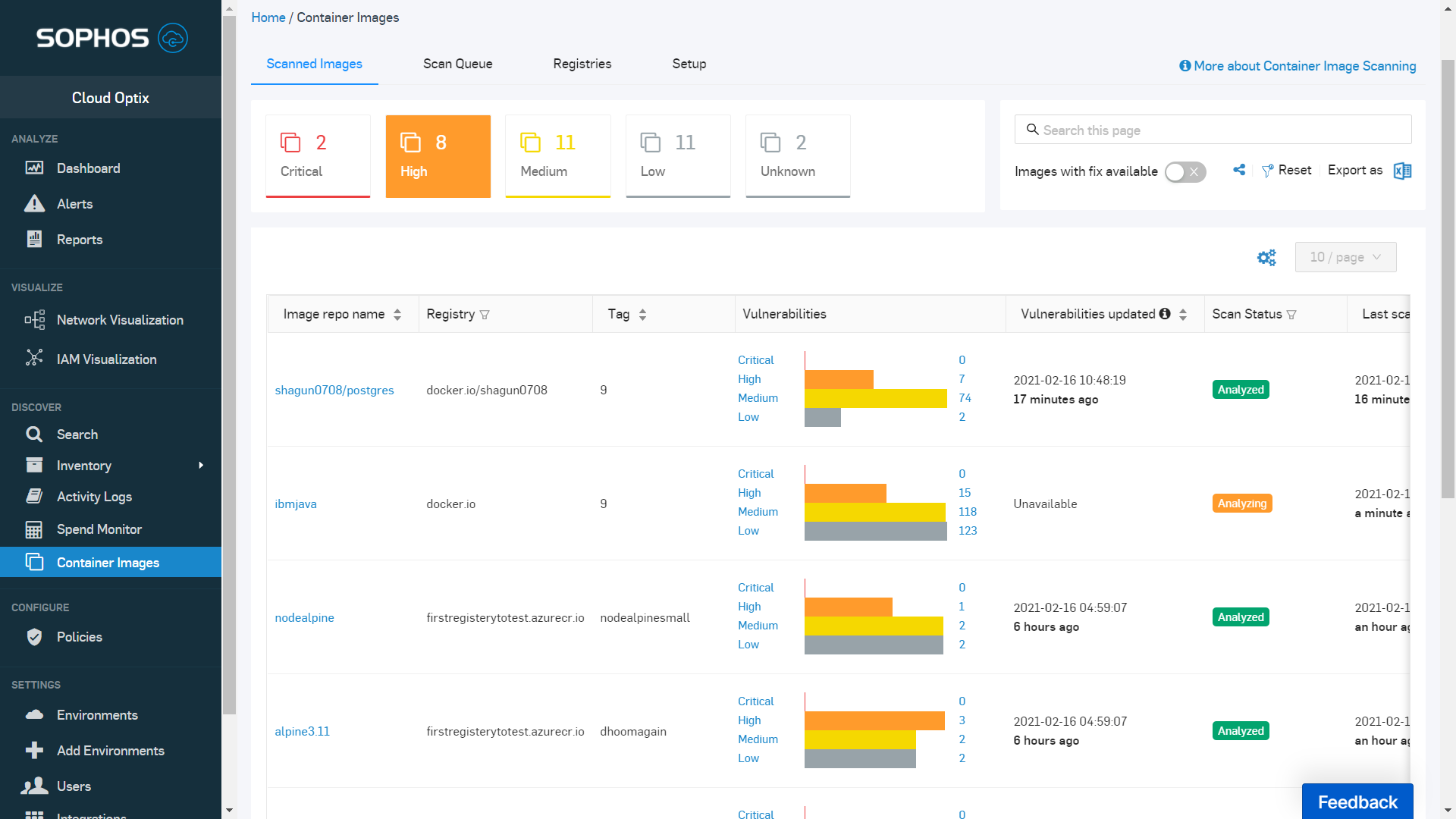
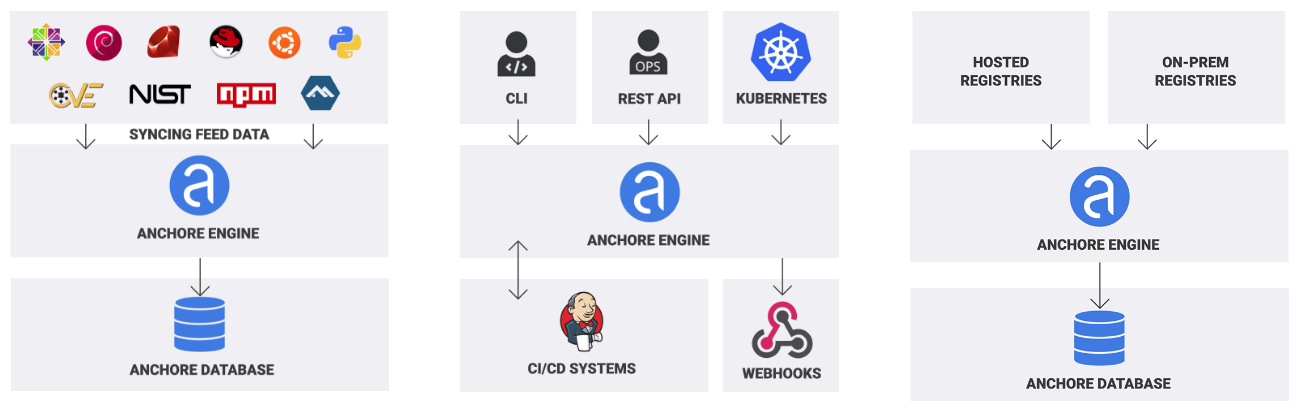
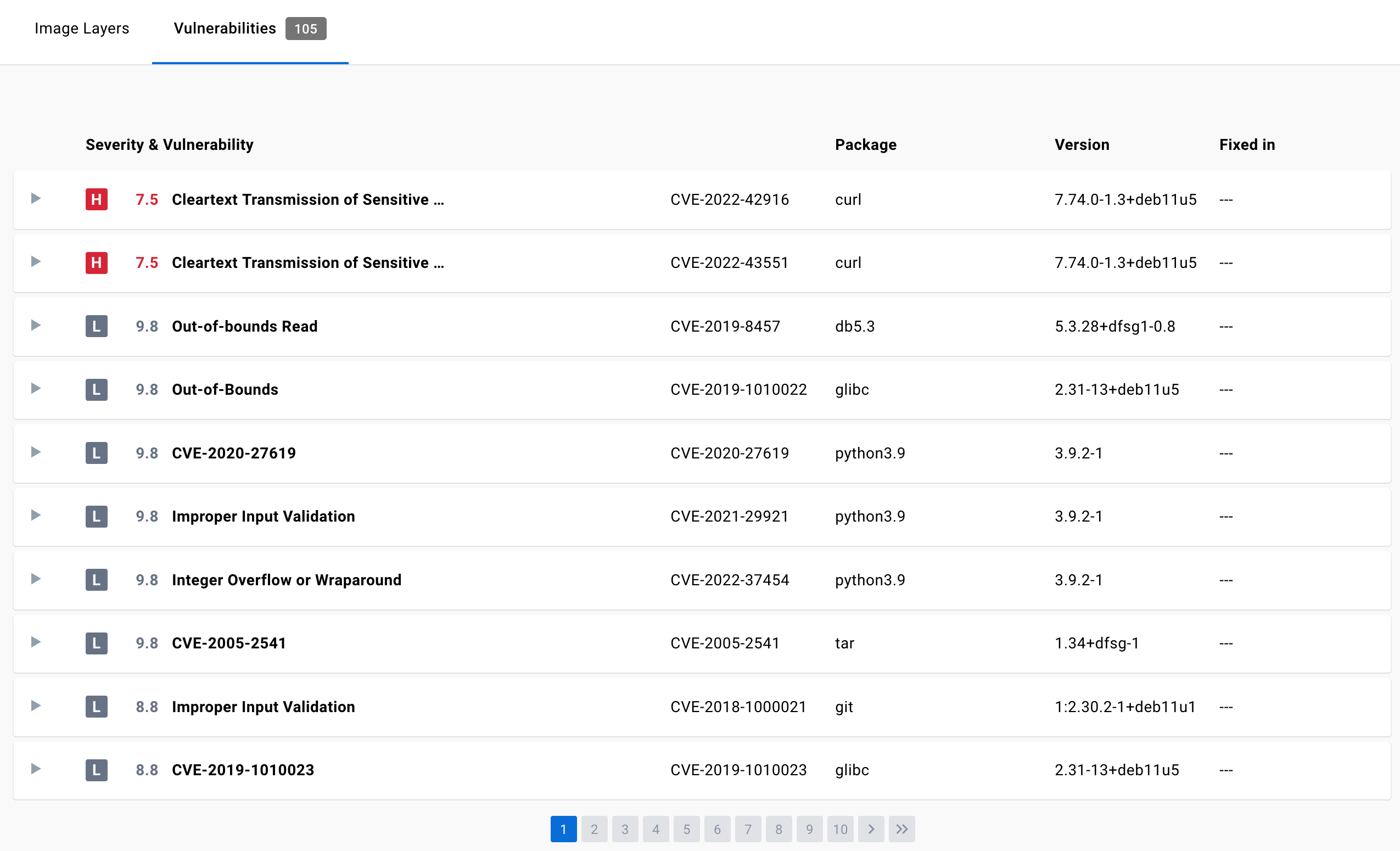
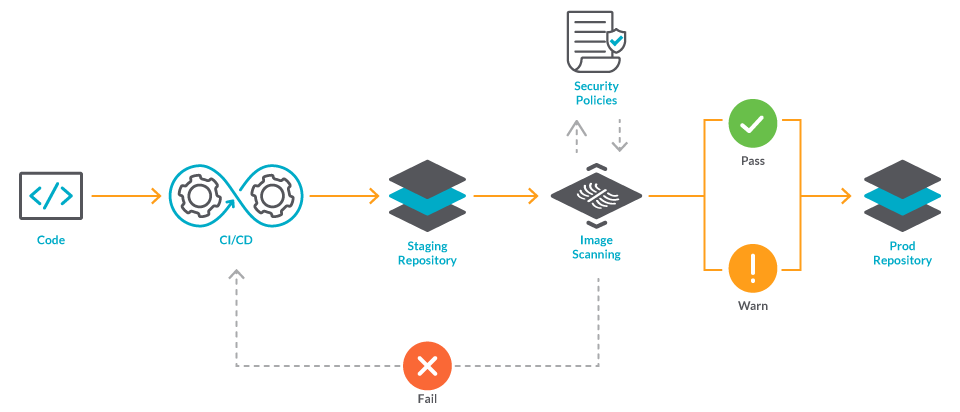
Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog
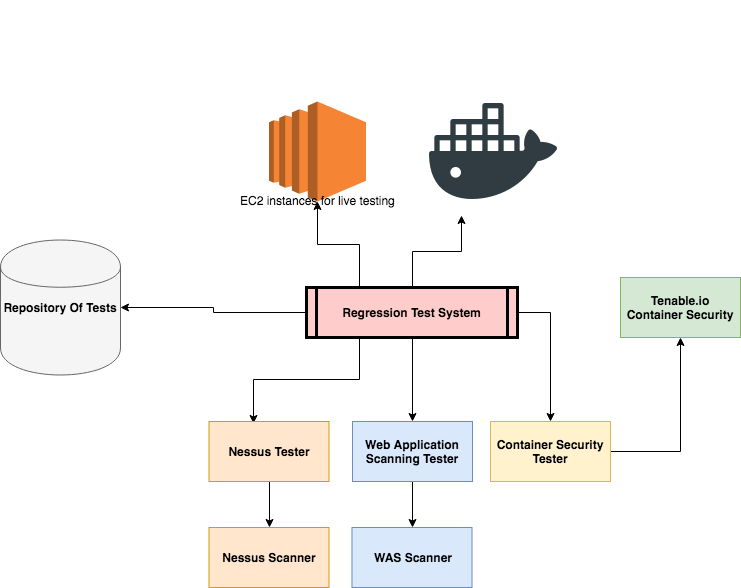
Automated Reconciliation of Vulnerability Detection Across Scan Engines | by Sasan Padidar | Tenable TechBlog | Medium





/filters:no_upscale()/news/2020/12/dockerhub-image-vulnerabilities/en/resources/1Screenshot%20from%202020-12-20%2014-54-56-1608456415853.png)