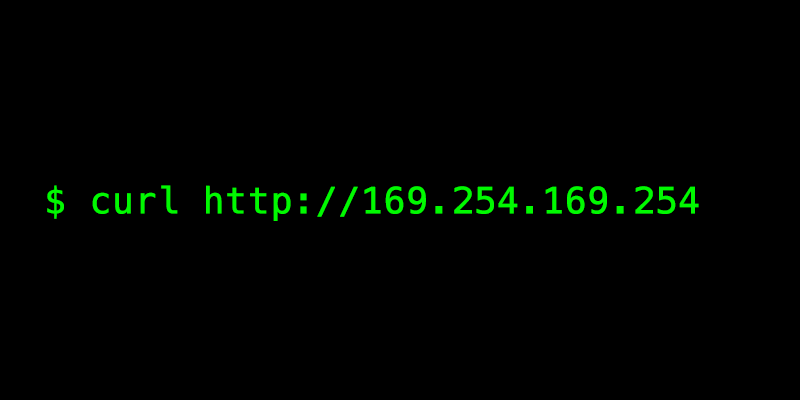
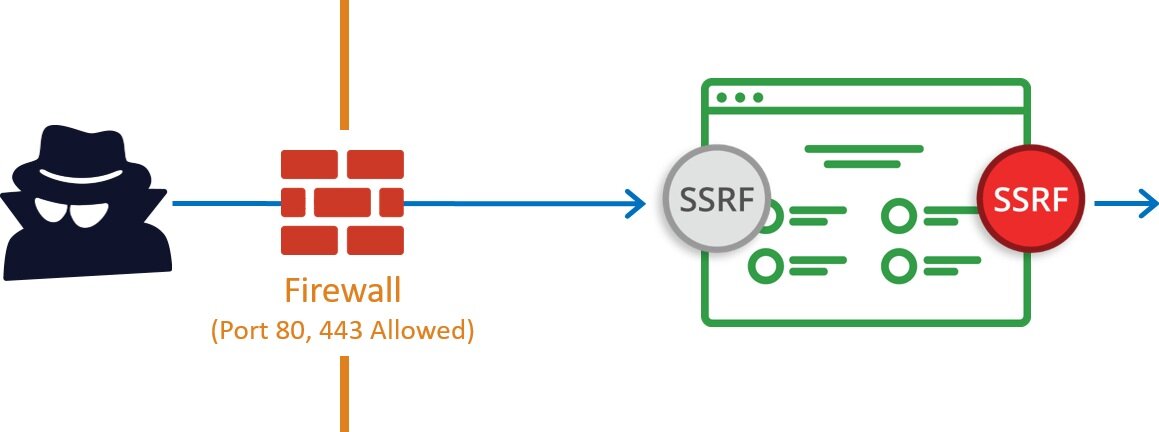
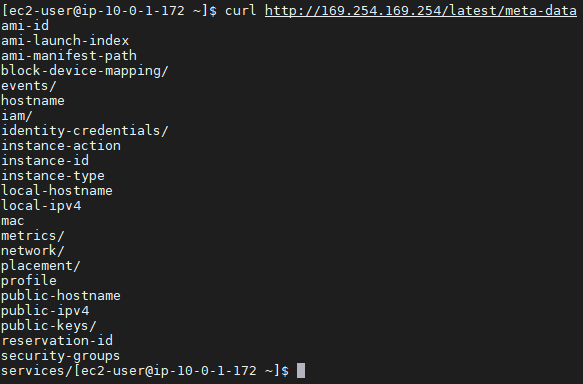
Server Side Request Forgery (SSRF) and AWS EC2 instances after Instance Meta Data Service version 2(IMDSv2) | by Riyaz Walikar | Appsecco

Capital One Breach: A Crime Board & A Case of Speculative Sleuthing | by Chetan Conikee | ShiftLeft Blog

Get started with automated metadata extraction using the AWS Media Analysis Solution | AWS Machine Learning Blog

Getting started with Version 2 of AWS EC2 Instance Metadata service (IMDSv2) | by Sunesh Govindaraj | Appsecco
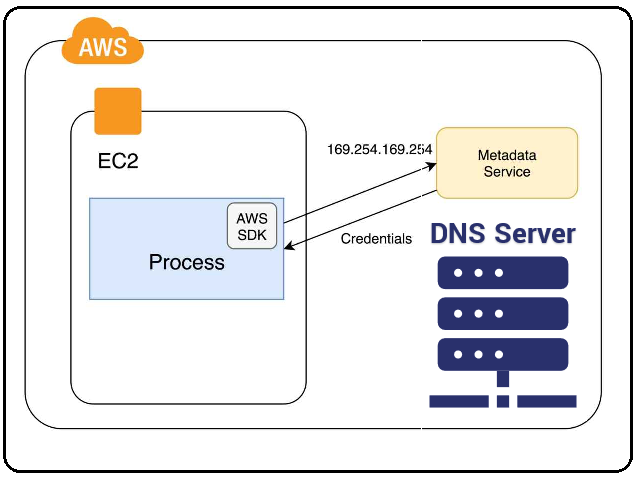
Detecting and hunting threats in AWS Cloudtrail logs and events with machine learning | Elastic Blog

Hunting for Capital One Breach TTPs in AWS logs using Azure Sentinel - Part I - Microsoft Tech Community
Netflix Information Security: Preventing Credential Compromise in AWS | by Netflix Technology Blog | Netflix TechBlog