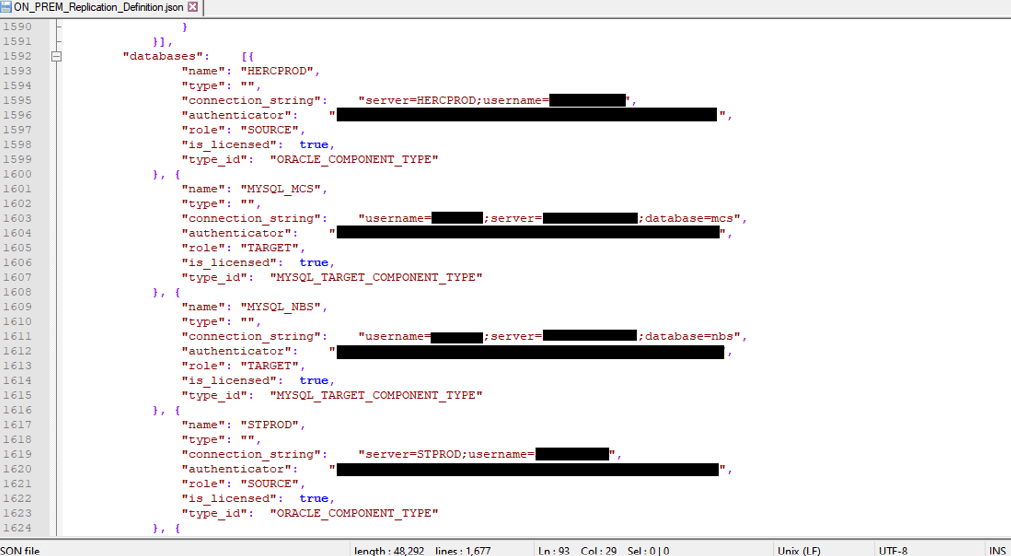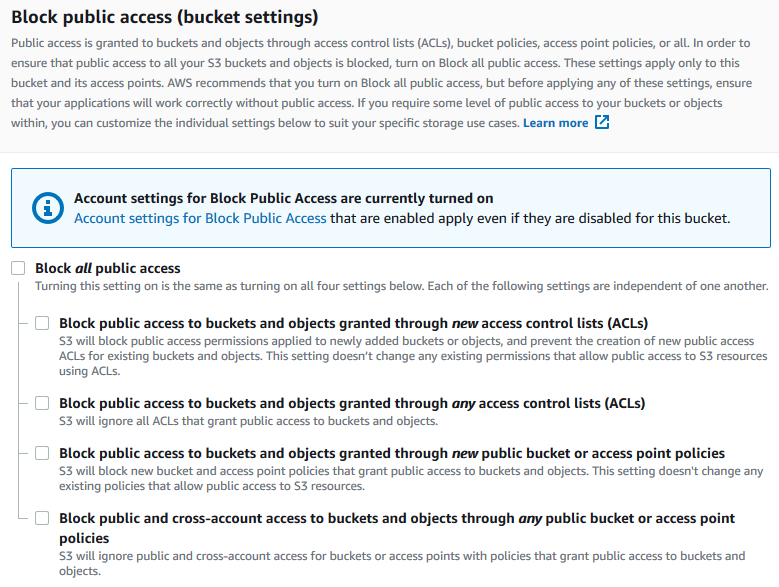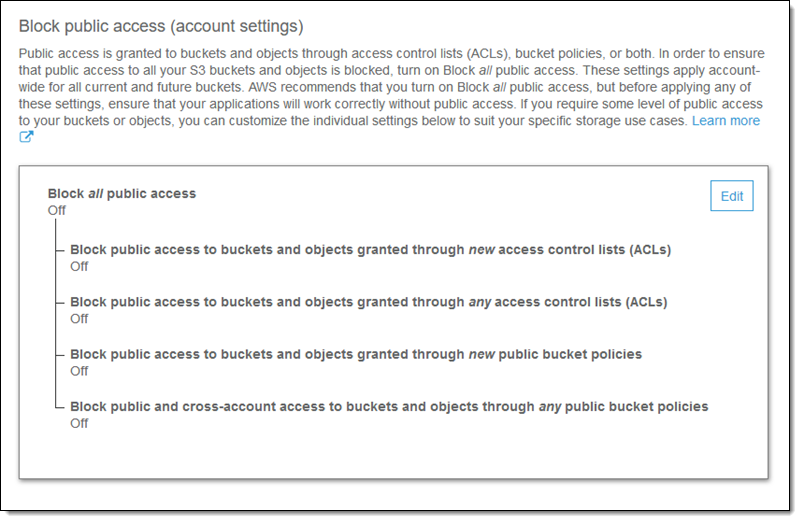
Amazon S3 Block Public Access – Another Layer of Protection for Your Accounts and Buckets | AWS News Blog

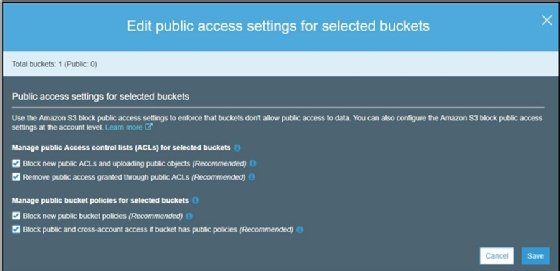
Strengthen the security of sensitive data stored in Amazon S3 by using additional AWS services | AWS Security Blog
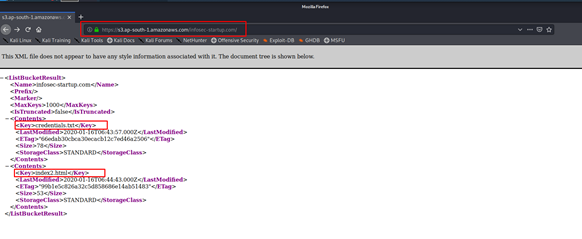
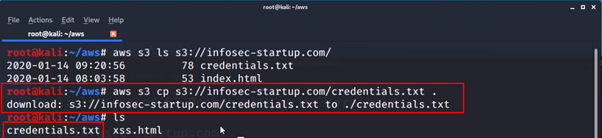
Misconfigured S3 Bucket Access Controls to Critical Vulnerability | by Harsh Bothra | InfoSec Write-ups