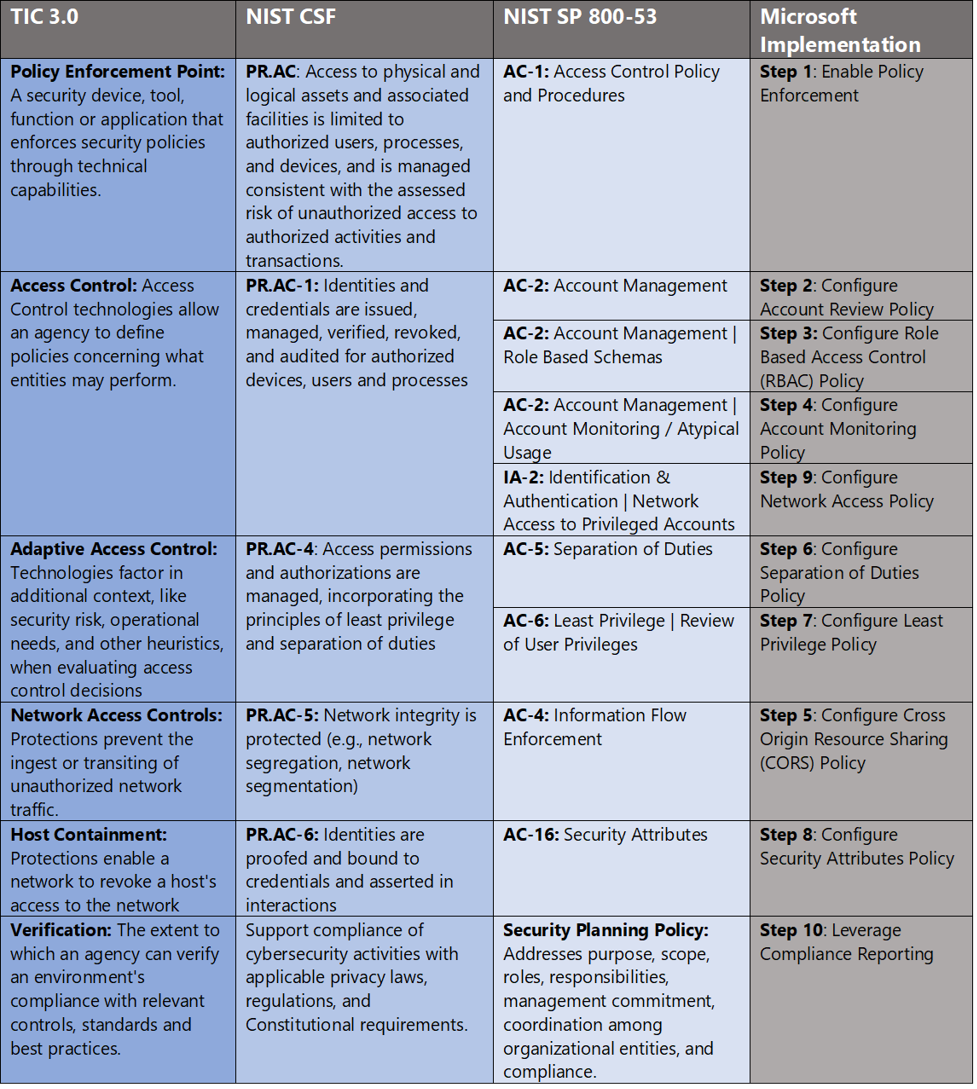
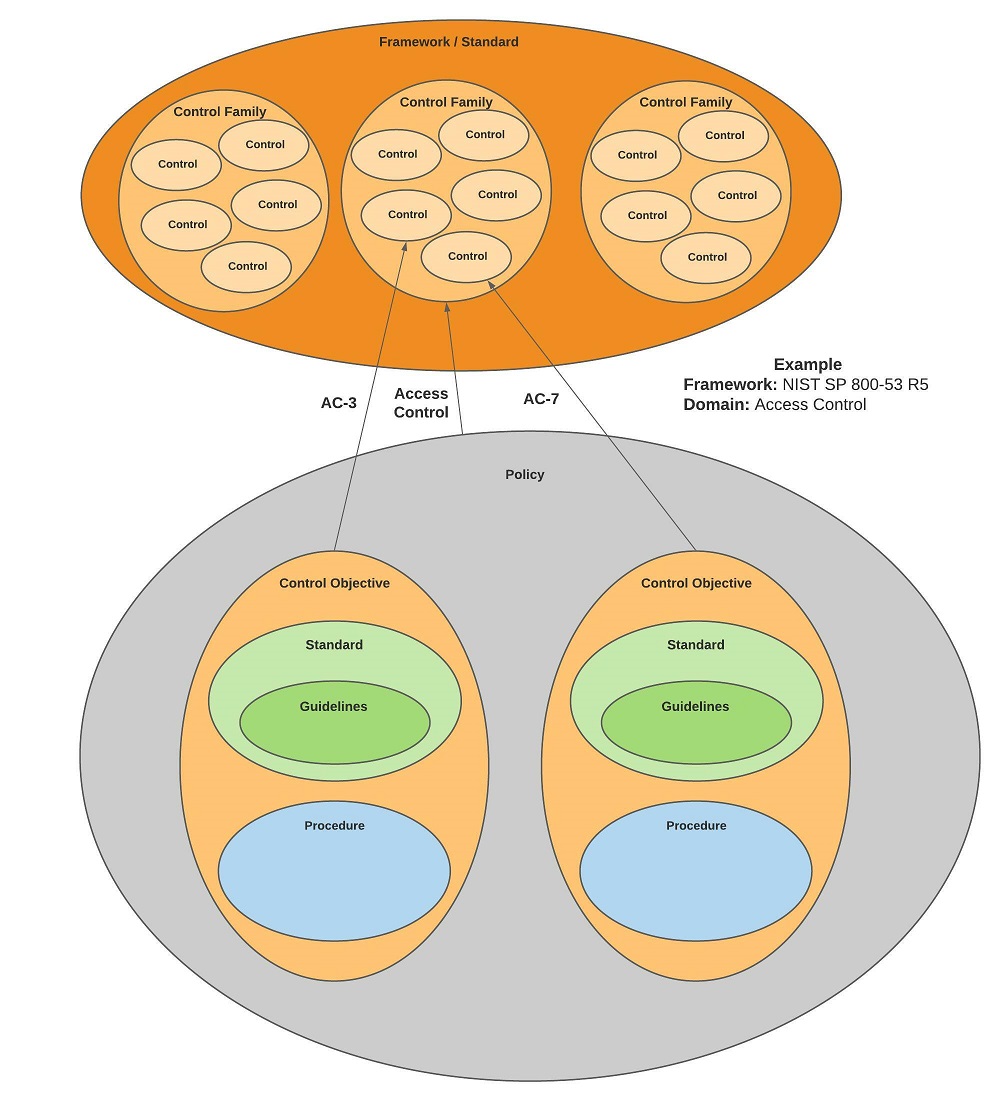
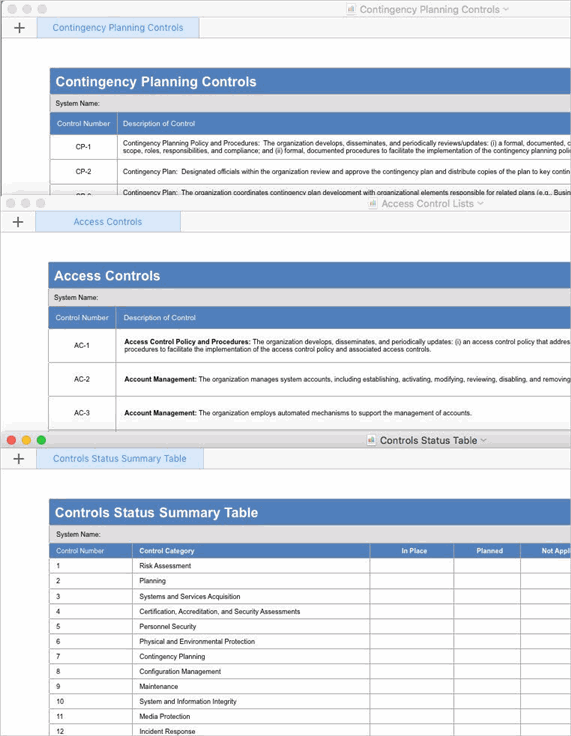
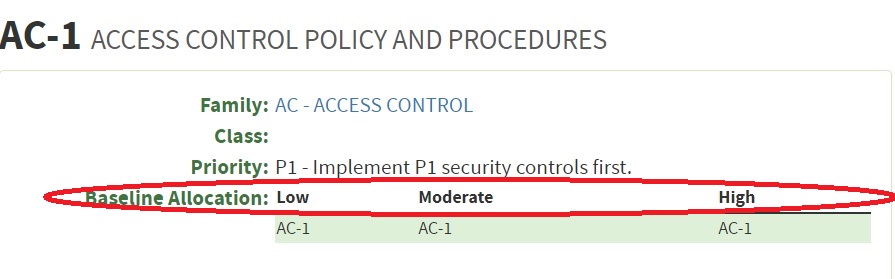
Meet critical infrastructure security compliance requirements with Microsoft 365 - Microsoft Security Blog
Excerpt of device specific checklist with derived security requirements | Download Scientific Diagram
Share our Security Control Profile · Issue #4 · canada-ca-terraform-modules/terraform-kubernetes-aks · GitHub

![PDF] Verification and Test Methods for Access Control Policies/Models | Semantic Scholar PDF] Verification and Test Methods for Access Control Policies/Models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1b2bd4561a8db9fe931faece1321a63981d3f3e8/53-Figure26-1.png)